Andy Marken’s Content Insider #190 – Insecurity
People Make Security Exploitation Too Easy
“When two hunters go after the same prey, they usually end up shooting each other in the back. And we don't want to shoot each other in the back.” – Col. Douglas Mortimer, “For a Few Dollars More (Per Qualche Dollaro I Piu)”, Constantin Film (1965)
NY Times writer, John Markoff, had just finished his book on the exploits/capture of hacker Kevin Mitnick about the same time we received a call from our boss at CERFnet (one of the first three ISPs in the U.S.) telling us we had to change our password because the fledgling West Coast arm of the Internet had been hacked.
We had 10 minutes to give him our new password that would be part of our online identity to access, contact the world.
That sucked!
We had just gotten rid of the mind-boggling CompuServe numbers and…well, we really liked that password.
Monco’s comment came to mind, “Think you people need a new sheriff,” but kept our mouth shut and changed the password.
Flash forward 20 plus years and it seems so inconsequential.
Sure, Internet security is an oxymoron like homeland security.
Security at work or on your own device is important as long as it doesn’t get in your way of doing things like talking with others, getting work done, playing games, watching videos, listening to music.
People don’t want to jump over a bunch of hurdles. They want speed, reliability.
Anything else and they’re outta’ there!
Big Business
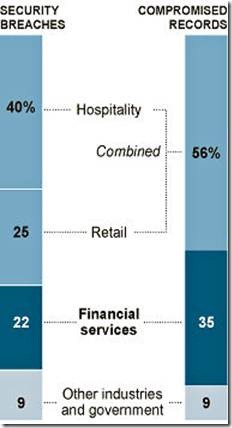
Last year, hacking was big business -- more than 3.8 million records compromised. And more than a third of them were held by banks, financial institutions.
Computer Hacking Problems by Industry, 2010
Prime Targets – Last year was not one that security experts want to relive, but they know the record number of attacks is only the beginning of even bigger breaches. Criminals are reaping big profits and kids are having fun flaunting their exploits to the point that even hackers are after hackers. Source – Verizon
The hack attacks may highlight user names/passwords, but those that don’t crave the publicity/notoriety are after the important stuff…credit card, financial records.
As Fernando pointed out, “That's the bank! As soon as I get some money, I'll put it in.”
So IT people have a pretty hard job…protecting us from ourselves.
Online Cash – While ecommerce sites revel in the fact that online sales are steadily growing, companies are investing heavily in closing holes and beefing up security to give customers greater confidence that they provide a safe place to do business. Some call it the cyberwar space they don’t want to talk about. Source - eMarketer
People who feel the most pressure are those involved in online sales sites.
They have to make it easy so you don’t abandon your shopping cart, but they also have to make you feel they’re protecting your junk.
Those selling locations – and most others – try but they’re outnumbered, outgunned.
The skilled IT people who weren’t cut (because finance said we don’t need those folks since we haven’t been penetrated) don’t have the weapons the Red Bull-drinking kids and growing criminal organizations have.
Plus hackers have more motivation to “show the system” or just plain greed.
Monco was motivated when he said, “Seems like a pretty good place for an ambush to me.”
The danger doesn’t matter to company management who want everyone working on, using the social net. That’s where the business of business is focused today.
Social Outreach
Today, we’re reaching out, staying in touch with friends, partners, customers all the time at home, on the road, at the office.
Open to Talk – Social media sites are attracting huge crowds of people who want to connect with people who share common ideas and interests. They are also attracting large numbers of hackers and cybercriminals who want to use that information to their advantage.
Hactivists and cybercriminals love social media because you share so much that they don’t even have to be half-way good at stealing/exploiting. We give them almost everything they want/need…and more.
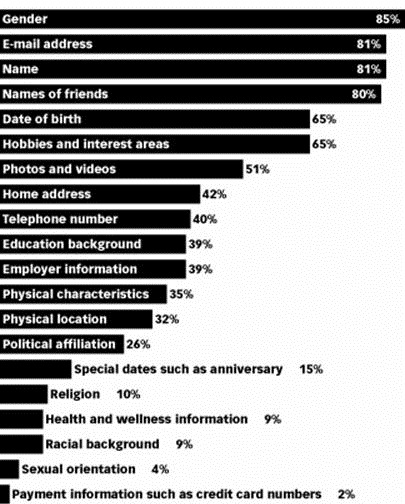
Information Users Share on Social Media
Sharing – Social site members seem to be willing to share as much information as necessary – and then some – to become part of the group. They might not share as much information in face-to-face meetings as they do on the Web; but since many have grown up online, open sharing is of minor concern. – Ponemon Institute
But there’s no need to beat yourself up for sharing so much.
Social media sites make really great targets for the cybercriminals because it may be a little more work (getting the information one user at a time) but the information has good resale value.
The sites have more holes than Swiss cheese.
LulzSec, Anonymous and just about anyone with decent skills and a few hacking tools can have a freakin’ ball creating havoc.
Leaky Web – Almost every location on the Web looks like a web to hackers. There are holes everywhere that people with just a few tools and half-way decent expertise can penetrate just to be mischievous, nasty or for personal gain. - comScore
The hackers seem to be of the mindset that we can do it the hard way or the easy way…your choice. Unfortunately, most folks make it way to easy for the kids/criminals to hook the over trusting, gullible or people who have visions of wealth doing nothing.
Nino warned them when he said, “Here are your guns without bullets.”
Waiting for Dinner – While hacktivists carry out their work to exploit and embarrass organizations, cybercriminals like to follow behind them to pick up morsels of valuable information and occasionally attack on their own for full-blown financial meals.
The personal attacks start out so warm and friendly. Before folks know it their identity has been picked clean.
Gotta’ Use Devices
Personal computers and notebooks were bad enough (or good enough, depending on which side of the Web you sat); but the growing popularity of mobile devices – smartphones and tablets – have made hacking and cybercrime even more fun, more productive.
The array of devices, the growing usage and security “opportunities” have made security an even bigger challenge for IT folks (responsible for blending the devices into the company infrastructure) and a richer opportunity for the hackers.
Your mobile device risks include:
-
Stolen password – mobile browsers tend to expose sensitive information (user name, password, account data) when they communicate with websites
-
Weak data protection – device manufacturers, service providers try to silo their core software, data from third-party apps but the silos are built with pretty weak mud
-
DoS Attack – Denial of Service is increasing because the mobile device software leaves the device vulnerable to attack to crash it by overloading memory
Of course, those “minor” problems are nothing compared to all the stuff you and thousands of other trusting folks store in the Cloud.
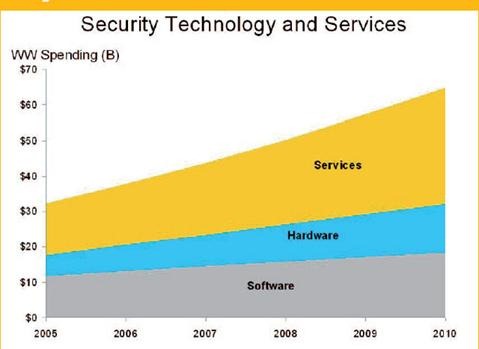
It’s no wonder that the security technology and services business is getting huge – fighting overwhelming odds but growing just the same.
Problems, Opportunities – The sale of security hardware, software and service has always been a “decent” business, but it has historically been a difficult sale because people just don’t like buying “life insurance.” But the coverage being given to the latest series of “victimless” activities has made security and content protection a higher priority with almost every organization/individual with connectivity. - IDC
While some people (i.e., the boss) want to lay all the responsibility of protection on IT people, there are things the rest of us can do to make it a little more difficult for the hacktivists and cybercriminals.
Focus, People. Focus!
First, realize you are on the Net, the Web and visible to the world.
Sites/services track, monetize what you do.
Sure, the service is free; but get real.
Act/communicate accordingly…the next Tweet, the next text message could easily end up on someone’s front page. When in doubt, they have a button for that…Delete.
As Col. Mortimer observed, “It's a small world.”
There are also a growing number of free, paid privacy, security products that allow you to manage the way companies (and others) track your online activities.
They include:
-
Secure data vaults (Dropbox, ain’t exactly secure) will collect, store your data for a fair price
-
Tracking protection services alert users when they are being monitored online
-
Reputation management services are becoming increasingly popular as individuals and parents get assistance in monitoring and controlling their online profiles
When you join a new site, service – free or paid – read the fine print.
The sub-mouse size type will tell you what they do with all your info and how you can jump through hoops to keep your info private.
Their lawyers include (bury) that to CYA (look it up in Wikipedia).
Trained Assistance
If you’re using your devices at the office, work with your IT/security people rather than around them.
Got a pet project you’ve just gotta’ get up there/out there that IT will only slow down if they get involved? Hacksters/cybercriminals love the “work-around” folks.
Those are probably the holes LulzSec used to get in so they could post their exploits.
Sure, security – personal, company, consumer – is lax because it just hasn’t been important…until now.
But the weakest part of it is the one hucksters/cybercriminals take advantage of most…the user.
All About You – Hardware, software and service organizations continue to beef-up their protection of content. The problem is, they haven’t figured out how to close the biggest source of vulnerability--the individual on the keyboard or device. – Dreamtime.com
As Monco said, “There seems to be a family resemblance.”
The attack one-upsmanship is the next phase of iNet, Web, mobile connectivity we’ve experiencing and it won’t end well.
You just don’t have to make it too easy for them!
As Fernando said, “You probably wouldn't like that other place as much, signor. At that place you'd stay up half the night shooting cockroaches.”
# # #
I will be giving a copy of the book, Social Media Judo, starring yours truly to three randomly-selected people who email me at john.obeto@absolutevista.com.
Should the winner prefer, a Kindle version of the book will be substituted once that becomes available.
This free offer ends on September 30, 2011 at midnight Mountain Time.