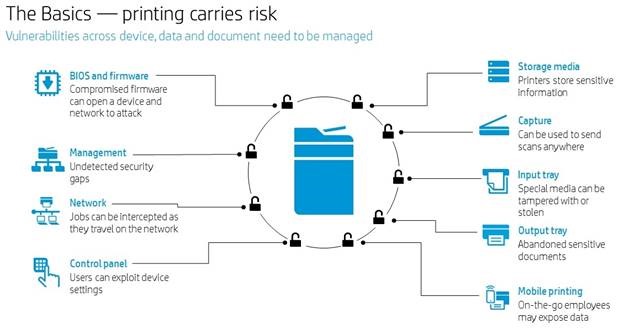
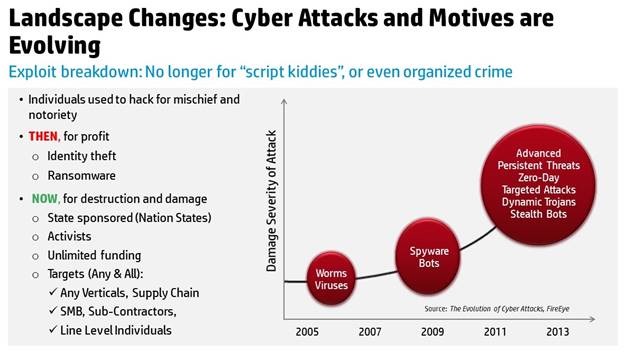
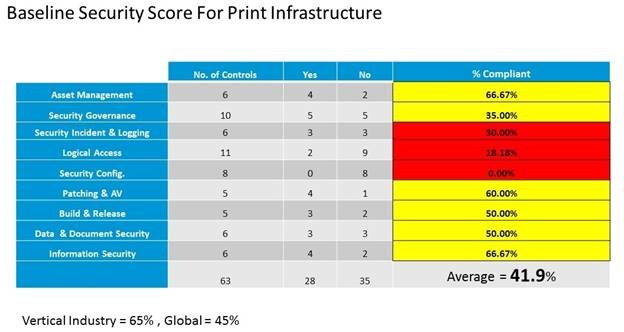
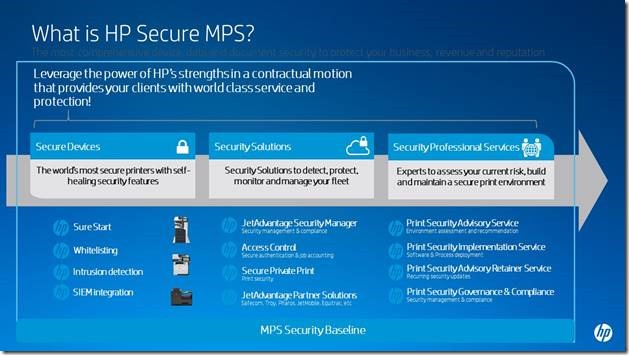
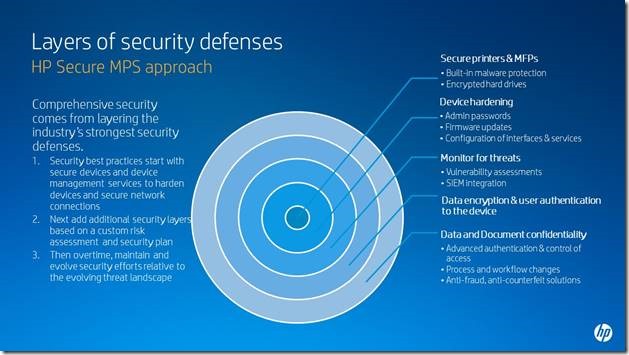
The Alternate World of Virtual Reality at CES

“I can carry nearly eighty gigs of data in my head.” – “Johnny Mnemonic,” Tristar, 1995
Even though industry analysts are lukewarm on the success of VR (virtual reality), you couldn’t tell it as you navigated around many of the booths during CES with HMDs (head-mounted displays) taking you into fantastic immersive worlds and games.
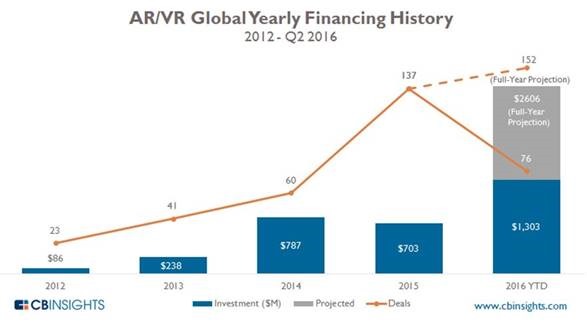
Ups, Downs – Gartner’s Hype Cycle reveals trends affecting start-ups and investments. When the interest is building, new folks rush to VCs and quickly get money to develop their barn burner. Then the MBA VCs realize too many folks are chasing the same rabbit so investments drop and reality settles in.
But it was hard to say “Whoa” when CES was so content-centric this year.
Jeezz, you were dodging folks stumbling around blindly with HMDs at every turn.
With the units strapped on, all I could think of was horses with blinders.
Leading up to the show, industry analysts were suddenly saying Whoa to VR and were lukewarm to the technology’s wild success forecasts for mind-twisting, fantastic immersive worlds and games.
The big problem was newbies, VCs (venture capitalists) and pitch people put VR in the same bucket with augmented (Pokemon Go) and anything with a headset. No wonder they couldn’t see the forest for the trees!

Whe-e-e-e
They were riding the consumer VR hype train that left the station when Oculus’ Palmer Luckey put on the Rift.
They didn’t know where the train was going, but they were getting on board!
Most of the publicists called the stuff in their booth the real VR thing--computer-tethered (Oculus Rift, HTC Vive, Sony and…) or smartphone clamp-on stuff (Samsung Gear, Google Daydream, Zeiss and a gaggle of others)--even if they were only showing 360 content.
Despite the enthusiasm slump, growth is on the horizon because the major processor folks (Intel, Nvidia, AMD, Qualcomm, Samsung) have already made a wholesale commitment to the new space.
And the major players (Alphabet, Facebook, Sony, Samsung, HTC) have jumped in with both feet.
When I caught up with him at the show, VR filmmaker Lewis Smithingham (30ninjas) said, “This is one of the few technologies in history that all of the major players have weighed in on and invested early. That’s had a profound effect on how quickly products that are solid and economic have become available.
“Unfortunately, it’s just been overhyped,” he added. “It will continue to grow, but probably won’t have such a giant spotlight until 2018.”
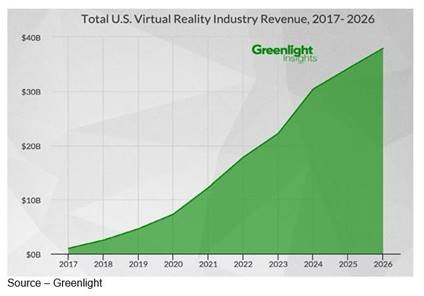
Huge Someday – VR is super cool and will be huge in a few years, but success seldom occurs overnight. The market requires a total ecosystem – hardware, software and content. Then it needs consumer acceptance beyond the early adopters. That requires more time than people want to recognize.
His estimates coincide with a recent report by Greenlight Insights that notes growth will be relatively modest for the next five years, becoming strong by 2026 ($38B in revenues).
Officials at Nvidia’s and Intel’s booths were more bullish during the show about how quickly the market will expand, noting:
-
the working tools are in place
-
every game developer is delivering or developing fast-moving, white-knuckle, immersive games
-
both firms have been working closely with Hollywood studios, and 2017 will mark the opening of nearly a dozen tentpole VR films
“We’ve spent the past few years working on the infrastructure development which is key to VR’s success,” a member of the Intel team noted. “Experience it just once and you know it’s going to be a category that is growing.”
Not Really New
Actually, VR has been the stuff of science fiction since the early 1900s with the development of the Link Trainer for pilots; and even earlier with 360-degree viewing. The Link Trainer saved the aviation industry billions of dollars and probably hundreds of lives.

Nip ‘n Tuck – While kids think VR was developed totally for their enjoyment, it has been invaluable in educating and training--especially in the healthcare industry. With the consumerization of the technology’s hardware and software, costs have come down quickly in these areas.
It wasn’t long before the educational community saw how it could enhance and enrich student training. Not as exciting as playing Wayward Sky or watching Invisible but then no one wants to be a surgeon’s first for an operation.
Folks at CES say the VR market could reach $10 billion by 2018.
The challenge is the market is segmented:
-
If you’re a heavy gamer or want to be in a fantastic, breathtaking movie; you’ll use a computer powered by NVidia, Intel or AMD or a game console. People who really care about visual quality know it takes power to move smooth, jitter/buffer-free VR.
-
If you like decent on-the-go gaming or brag-about-it videos from YouTube or Facebook Live, slap an HMD on your smartphone and go for it. The biggest issue is going to be your smartphone because the display and processor inside can make a huge difference. In addition, the units generate a lot of phone heat and put a tremendous drain on the battery.
Most market analysts treat VR as one big bucket.
The Tractica team is one of the few that views mobile (hardware, software and use) as a unique market.
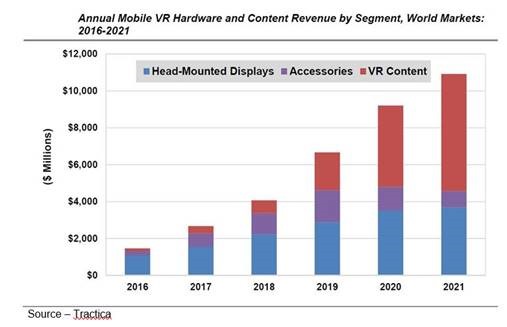
Mobile VR – The emerging VR market isn’t a one-solution-fits-all. Many feel that over the long haul smartphone HMD VR will be the dominant viewing/playing platform.
True there will be about 3B smartphone users worldwide by the end of the year; and only about 2B PCs, but the immersive quality difference between the two is night and day.
Game On
CES attendees seemed to enjoy the active participation with the VR games; pitting themselves against zombies, aliens, bad guys and spooky environs.
Standing next to the PlayStation VR demo, one of the Sony folks explained that the immersive and involved play that is possible with VR will drive the rejuvenation and expansion of the video game market.
“Nothing compares to the thrill, excitement you experience when playing one of the new VR games … nothing. Gaming will make VR mainstream!” he emphasized.
I didn’t want to burst his bubble but I’m pretty certain movies, video (very good content) will dominate VR entertainment. But then, I don’t do games!
Still, when it comes gameplay, I had to sanity check with someone who really knows the market so I checked in with Mark Poppin, of BabelTechReviews, who has been testing games on Nvidia-powered PCs as well as consoles and other systems.
He pointed out that VR gaming can’t be judged by the initial offerings because many of them were “worse than bad.”
A lot of good VR games are rolling out and our forum has been very excited about the strength of the graphics and opportunities in the fresh releases. The good games really point out the problems of stuff that’s just been thrown together. Good VR lets you become part of the game and makes it different, more challenging every time you put on your HMD,” he explained.
"Thank Heaven for VR game reviewers and social media to point the good ones out," He added.
Despite the shortcomings of smartphone HMDs for game play, even VR filmmaker Smithingham enjoys them for a break from work.
VR Storytelling
However, for the great VR movies scheduled for release this year and for most VR video projects (documentaries, travelogues and immersive and personalized entertainment), he believes HMDs will have to be tethered to a PC … the more power the better!
“Mobile works very well for things like streaming YouTube and Facebook videos,” Smithingham noted. “You know, the social media stuff and 360- degree marketing. But right now, there’s a limitation with mobile. You’re sucking up 4 to 5 times the bandwidth 4K video requires. They have to overcome the laws of physics.”
If you’re like my kid, you’ll want both – the on-the-go smartphone HMD and the gotta-be-in-the-middle-of-it – with his PC HMD. Try both flavors and you’ll “know” which is best for the kind of stuff you want to play/view.
Of course, there were rumors that next year; we’ll see a standalone (not tethered to something) HMD with its own display, processing and wireless connectivity. But that’s only a rumor.
Regarding the movies we viewed on the show floor, one thing was apparent, “This year’s VR movies and video experiences are going to be freakin’ awesome!”
And with the industry’s drive to consumerize VR, the reduction of hardware/software costs has dramatically accelerated.
Capture Tools
It was perhaps most apparent with the wide range of 360/VR cameras being shown.
Jaunt, Nokia, Lytro, GoPro’s Omni and Sphericam’s camera that includes timesaving automatic stitching software were evident at the show and looked like overkill for the consumer shoot/view event.
There was a wide array of $100 - $500 consumer level 360-degree cameras shown by Samsung, LG, Alli, Bubl, Kodak, Giroptic, Nikon, Ricoh and 360fly as well as a number of cute VR attachments for your smartphone.
While these will appeal to YouTube and Facebook video folks, a major concern is that the VR experience might impair widespread acceptance and enjoyment of virtualized video.
Major studios like Fox, Disney, MGM and Lionsgate; as well as leading-edge VR filmmakers shoot and review scenes and content multiple times to ensure the final content doesn’t produce an “argument between the mind/body” which can result in nausea and headaches.

Pro Cameras – While there were a bunch of low-cost 360 cameras unveiled at CES, Lewis Smithingham (r), president of 30 ninjas, found units like the Shericam 2 being held by company founder Jeff Martin to be the preferred choice for serious filmmakers.
Sphericam’s Jeff Martin (founder) noted that the film experiences people have are totally different from films the industry has been producing for more than 100 years where the producer controls the storyline and flow of the film.
“It’s not like you slap a GoPro rig in a racecar and drive around the track,” he cited. “That’s fun once but a really good VR film puts the viewer squarely in the center of the story and he/she controls how the story unrolls. Filmmakers are learning how to guide the viewer with little plot hints – like Hansel & Gretel bread crumbs – but it requires experimentation to get it right.”
Content Plus
Sphericam’s founder Jeff Martin noted that the film experiences people have are totally different from films the industry has been producing for more than 100 years where the producer controls the storyline and flow of the film.
“It’s not like you slap a GoPro rig in a racecar and drive around the track,” Martin said. “That’s fun once but a really good VR film puts the viewer squarely in the center of the story and he/she controls how the story unfolds. Filmmakers are learning how to guide the viewer with little plot hints – like Hansel & Gretel bread crumbs – but it requires experimentation to get it right.”
Content Plus
Strictly for VR research purposes at the show, I stopped by the Naughty America VR booth. I think this is a return of adult entertainment to CES, which as I recall was encouraged to seek another venue about 10 years ago.
Ian Paul, Naughty America CIO, noted that according to Google Trends (they track everything), interest in the VR subject area has increased 9,900 percent in the last 17 months.
At CES, the company went to great lengths to point out they were platform agnostic. Their “members” could use the HMD of choice -- Samsung Gear VR, HTC Vive, Oculus Rift, Google Daydream, Zeiss VR One, Sony PlayStation VR. They even encouraged headset manufacturers to swing by and see how well their gear delivered.

We politely declined to check the content – honest – after one individual summed up his experience as … “Awkward!”
To compensate for the massive streaming downloads to mobile HMDs, the company used adaptive streaming technologies.
But we prefer immersive entertainment that we can talk about in mixed company and our kids can participate in like Gone Girl, X-Men: Days of Future Past, 28 Days Later, Die Hard, Predator, Office Space, Martian VR, Jurassic World VR and the new stuff coming out this year.
We got hooked on the possibilities of VR films after seeing early demos two years ago at SMPTE and the quality of work students had created for this year’s conference.

Getting it Right – Lewin and his team spent hours shooting, stitching and editing their work on Invisible to get the content just right for the viewer to control the storyline using Nvidia-powered systems and lots of fast SSD (solid state drive) storage.
And after seeing the work Smithingham had done for Conan 360 and Don Liman’s recently released Invisible mini-series, it’s easy to see why filmmakers say they have only scratched the surface of what they and the viewer can do with the technology.
The foundation has been built and the games, video content and applications are available; but the ramp-up of hardware/system sales will take a few years.
That’s probably why folks formed three groups just before CES:
-
GVRA (Global Virtual Reality Association)
-
CTAWM (Consumer Technology Association Working Group)
-
VRIF (Virtual Reality Industry Forum)
The first is hellbent to educate the consumer about VR hardware (and increase sales).
The second was formed to provide “ecosystem-wide leadership” as new stuff is developed/released. I guess that’s why the first thing they’re going to do is develop a glossary of AR/VR definitions.
VRIF seems to be more focused on open industry standards. They advocate a consensus for the creation of an interoperable, end-to-end ecosystem that will give filmmakers (and game developers) non-proprietary tools to produce content folks can distribute (monetize) that people can use/enjoy.

That’s what will make Johnny Mnemonic and everyone else say, “I want to get online... I need a computer!”
But as CES folks said, Whoa!”
# # #