BYOD is Bad for IT, Great for Bad Folks
“I'm drowning here, and you're describing the water!” – Melvin Udall, “As Good as it Gets,” Tristar, 1997
Unless it was just yesterday, it’s probably tough to remember your first day on your job.
You know, after your HR briefing you were shown your desk, your computer and, if you did a lot of business travel, your Blackberry. Then you were thrown in the deep end to sink or swim.
Today, you get your workspace and set up your tools – your notebook, your smartphone, your iPad. HR sends you the link to policies/procedures, videos.
You’re in the deep end.
Frank Sachs takes it all in stride, “I grew up in hell! My grandmother has more attitude than you!”
It’s called the consumerization of IT or BYOD (bring-your-own-device) workforce.
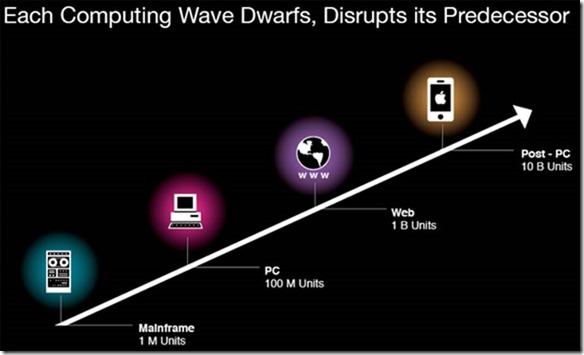
Humans in Center – Each new wave of technology dwarfs its predecessor. PCs dwarfed mainframes, which in turn were subordinated by the Web which opened the door for mobile, lightweight digital devices. The new devices are extensions of the owner, which is why they are vital in our home/office environment. Source – Mark Sigal
It came about slowly, insidiously, naturally and everyone has their opinion on how it happened:
- Millenials who started their jobs and grew up with notebooks in their backpack, phones in their pockets were accustomed to always being in contact with everyone, anytime, anywhere.
- The Blackberry was cool – for its time – phone/email always with them but it was rigid to use; and let’s admit it, communications were ugly.
- The boss got a sexy new iPhone - the guy/gal wanted to be on an equal standing with his/her kids -- and was determined to use it no matter what and insisted IT support it. That opened the door and everyone wanted to be as hip, productive as the boss.
Our vote goes for the last reason; but the others sure encouraged it.
Boss Opened the Door
Today, almost everyone in the organization has their personal tech gadgets – iPhones, iPads, notebooks/ultrabooks, Android device.
BYODs – When the doors opened for people to bring in their own devices for work and home, people did … in record numbers. It usually started innocently enough by the boss or new millennial always-connected employees; but the flood soon proved to bring everyone in the organization along. It will only continue
And they expect to have the devices connected to the corporate network so they can manage their personal lives and get their work done.
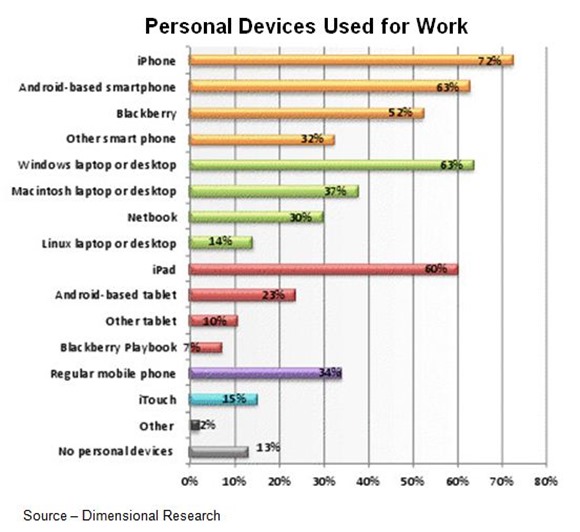
A recent survey by Dimensional Research of IT executives found:
- 88 percent of survey respondents want to have a policy in place regarding personal devices
- 82 percent are concerned about the use of personal devices for work purposes
- 64 percent are not confident that they know of all personal devices being used for work purposes
- 60 percent reported a greater demand for support of Mac OS X since the introduction of the Apple iPad and iPhone
- 59 percent reported that personal devices have created the need for organizations to support multiple operating systems
- 32 percent admit that employees use unauthorized personal devices and applications to connect to their network
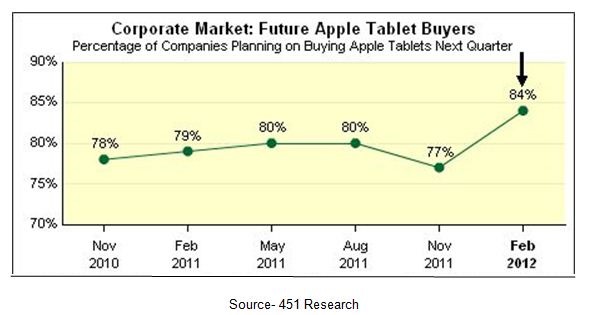
Even before Apple rolled out the new iPad, corporate sales were doing “okay.”
Seeing that his was on backorder, Simon Bishop mumbled, “So the life that I was trying for is over, the life that I had is gone, and I'm feeling so damn sorry for myself that it's difficult to breathe.”
Market of One for Now – It’s been three generations and as many years and the Apple iPad still has no significant competitor. One of the reasons is obviously that it just does what it is supposed to do the way you want it to do it. But more importantly, its walled garden has good apps that IT people (and others) sorta’, kinda’ trust.
With the new units hitting the stores and apps cropping up everywhere with no serious competitor in sight, people in all businesses/services can’t wait to get their hands on the new iPad.
And they have all the best reasons why they need it now.
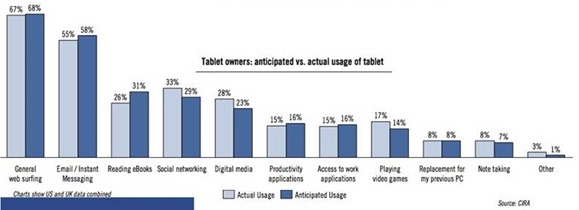
Business Users – While most “consumers” bought their iPads to play games, read materials and watch videos; business people chose them for more practical, business-oriented applications. And, as you can see, most folks used them as they planned.
But their iPads are additive, not replacements because:
- They Aren’t Smartphones – handsets have a lot more apps and you can make a phone call with something that pops into your pocket
- Tablets are good travel/business companions for working with email, taking notes more easily, read books/news, watch movies on a decent size screen, play games
- Laptops/notebooks are still ideal when it comes to getting work done. Sure you can add a keyboard and larger screen or take along both and use them accordingly
- Ultrabooks (think Macbook Air) give an ultra-slim design, laptop power, near-table battery life, very good storage/work capacity
- Most business users like to get at least a couple of years of work from their devices, especially when the new one is “a little better” -- not revolutionarily different/insanely better
BYOD blurs the lines between work and personal lives; so rather than eliminating one or more devices, we now carry three.
There is a lot of engineering going on at Apple as well as Intel and its partners that will merge the tablet touch screen look/feel with ultrabooks. Then we may be able to lighten our load with only two devices; but that seems to be two or three years away.
Security Holes Grow
Of course that won’t solve the biggest challenge IT has today, protecting the organization’s sensitive assets – data.
Bad Guys, Gals – While the old days were marked by individuals targeting organizational networks, mobile devices changed all that. It’s just too easy to hack/slash a mobile device today. At the same time, the security requirements for IT continue to grow.
For example, our mobile data capacity is:
- Smartphone – 32GB
- iPad – 64GB
- notebook – 500GB and when we swap the “heavy” unit for an SSD ultrabook, it will probably be 240GB
So?
All of that capacity holds a treasure-trove of valuable personal/company data that hackers, whackers and cyber thieves would love to have. Others carry around even more valuable corporate data on their devices.
And if you didn’t know it, your company’s biggest security risk is you and your BYOD home/work devices.
As Simon Bishop noted, “The best thing you have going for you is your willingness to humiliate yourself.”
Recently, there have been a number of articles in the New York Times and other media regarding mobile device loss/theft and tapping into the device(s) to extract critical information or worse.
A couple of years ago on a family trip, our son whipped out his notebook to make a point of how poorly people secure their computers. He used the airport’s free Wi-Fi and get onto/into six computers … it took no time at all!
He proved his point.
Security Checkpoints
Recent reports point out that people who regularly do business in China go “device naked.”
That’s a little drastic for most instances; but as we consumerize IT, closing the holes is proving to be increasingly difficult.
It’s tough to change personal habits. But with spies, fraudsters and con artists becoming bolder and better, employees have to do more to protect confidential, sensitive information.
That means across town, across the country or halfway around the globe.
Hacking the corporate network is still fun for black hatters; but the folks who want the important, valuable stuff have a much easier, much better target that’s really easy to hit … employees.
Well-intentioned employees, people who download questionable apps and folks who work around security hurdles are much easier opportunities to work with.
However, the company saves money because it’s “your” device and you’re able to blend your personal and work life with some of the coolest tools on earth.
It’s just that sometimes you may want to hold them at more than arm’s length!
Looking at the total situation, Frank Sachs commented, “If there's a mental health organization that raises money for people like you, be sure to let me know.”
G. Andy Marken is founder and president of Marken Communications